The UM Gateway
Copyright © 2007 - 2014 Informatica Corporation
March 2014
Informatica Ultra Messaging
Version 5.3
March 2014
Copyright (c) 1998-2014 Informatica Corporation. All rights reserved.
This software and documentation contain proprietary information of Informatica Corporation and are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright law. Reverse engineering of the software is prohibited. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise) without prior consent of Informatica Corporation. This Software may be protected by U.S. and/or international Patents and other Patents Pending.
Use, duplication, or disclosure of the Software by the U.S. Government is subject to the restrictions set forth in the applicable software license agreement and as provided in DFARS 227.7202-1(a) and 227.7702-3(a) (1995), DFARS 252.227-7013(c)(1)(ii) (OCT 1988), FAR 12.212(a) (1995), FAR 52.227-19, or FAR 52.227-14 (ALT III), as applicable.
The information in this product or documentation is subject to change without notice. If you find any problems in this product or documentation, please report them to us in writing.
Informatica, Informatica Platform, Informatica Data Services, PowerCenter, PowerCenterRT, PowerCenter Connect, PowerCenter Data Analyzer, PowerExchange, PowerMart, Metadata Manager, Informatica Data Quality, Informatica Data Explorer, Informatica B2B Data Transformation, Informatica B2B Data Exchange Informatica On Demand, Informatica Identity Resolution, Informatica Application Information Lifecycle Management, Informatica Complex Event Processing, Ultra Messaging and Informatica Master Data Management are trademarks or registered trademarks of Informatica Corporation in the United States and in jurisdictions throughout the world. All other company and product names may be trade names or trademarks of their respective owners.
Portions of this software and/or documentation are subject to copyright held by third parties, including without limitation: Copyright DataDirect Technologies. All rights reserved. Copyright (c) Sun Microsystems. All rights reserved. Copyright (c) RSA Security Inc. All Rights Reserved. Copyright (c) Ordinal Technology Corp. All rights reserved.Copyright (c) Aandacht c.v. All rights reserved. Copyright Genivia, Inc. All rights reserved. Copyright Isomorphic Software. All rights reserved. Copyright (c) Meta Integration Technology, Inc. All rights reserved. Copyright (c) Intalio. All rights reserved. Copyright (c) Oracle. All rights reserved. Copyright (c) Adobe Systems Incorporated. All rights reserved. Copyright (c) DataArt, Inc. All rights reserved. Copyright (c) ComponentSource. All rights reserved. Copyright (c) Microsoft Corporation. All rights reserved. Copyright (c) Rogue Wave Software, Inc. All rights reserved. Copyright (c) Teradata Corporation. All rights reserved. Copyright (c) Yahoo! Inc. All rights reserved. Copyright (c) Glyph & Cog, LLC. All rights reserved. Copyright (c) Thinkmap, Inc. All rights reserved. Copyright (c) Clearpace Software Limited. All rights reserved. Copyright (c) Information Builders, Inc. All rights reserved. Copyright (c) OSS Nokalva, Inc. All rights reserved. Copyright Edifecs, Inc. All rights reserved. Copyright Cleo Communications, Inc. All rights reserved. Copyright (c) International Organization for Standardization 1986. All rights reserved. Copyright (c) ej-technologies GmbH. All rights reserved. Copyright (c) Jaspersoft Corporation. All rights reserved. Copyright (c) is International Business Machines Corporation. All rights reserved. Copyright (c) yWorks GmbH. All rights reserved. Copyright (c) Lucent Technologies. All rights reserved. Copyright (c) University of Toronto. All rights reserved. Copyright (c) Daniel Veillard. All rights reserved. Copyright (c) Unicode, Inc. Copyright IBM Corp. All rights reserved. Copyright (c) MicroQuill Software Publishing, Inc. All rights reserved. Copyright (c) PassMark Software Pty Ltd. All rights reserved. Copyright (c) LogiXML, Inc. All rights reserved. Copyright (c) 2003-2010 Lorenzi Davide, All rights reserved. Copyright (c) Red Hat, Inc. All rights reserved. Copyright (c) The Board of Trustees of the Leland Stanford Junior University. All rights reserved. Copyright (c) EMC Corporation. All rights reserved. Copyright (c) Flexera Software. All rights reserved. Copyright (c) Jinfonet Software. All rights reserved. Copyright (c) Apple Inc. All rights reserved. Copyright (c) Telerik Inc. All rights reserved.
This product includes software developed by the Apache Software Foundation (http://www.apache.org/), and/or other software which is licensed under various versions of the Apache License (the "License"). You may obtain a copy of these Licenses at http://www.apache.org/licenses/. Unless required by applicable law or agreed to in writing, software distributed under these Licenses is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the Licenses for the specific language governing permissions and limitations under the Licenses.
This product includes software which was developed by Mozilla (http://www.mozilla.org/), software copyright The JBoss Group, LLC, all rights reserved; software copyright (c) 1999-2006 by Bruno Lowagie and Paulo Soares and other software which is licensed under various versions of the GNU Lesser General Public License Agreement, which may be found at http:// www.gnu.org/licenses/lgpl.html. The materials are provided free of charge by Informatica, "as-is", without warranty of any kind, either express or implied, including but not limited to the implied warranties of merchantability and fitness for a particular purpose.
The product includes ACE(TM) and TAO(TM) software copyrighted by Douglas C. Schmidt and his research group at Washington University, University of California, Irvine, and Vanderbilt University, Copyright (c) 1993-2006, all rights reserved.
This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit (copyright The OpenSSL Project. All Rights Reserved) and redistribution of this software is subject to terms available at http://www.openssl.org and http://www.openssl.org/source/license.html.
This product includes Curl software which is Copyright 1996-2007, Daniel Stenberg, <daniel@haxx.se>. All Rights Reserved. Permissions and limitations regarding this software are subject to terms available at http://curl.haxx.se/docs/copyright.html. Permission to use, copy, modify, and distribute this software for any purpose with or without fee is hereby granted, provided that the above copyright notice and this permission notice appear in all copies.
The product includes software copyright 2001-2005 (c) MetaStuff, Ltd. All Rights Reserved. Permissions and limitations regarding this software are subject to terms available at http://www.dom4j.org/ license.html.
The product includes software copyright (c) 2004-2007, The Dojo Foundation. All Rights Reserved. Permissions and limitations regarding this software are subject to terms available at http://dojotoolkit.org/license.
This product includes ICU software which is copyright International Business Machines Corporation and others. All rights reserved. Permissions and limitations regarding this software are subject to terms available at http://source.icu-project.org/repos/icu/icu/trunk/license.html.
This product includes software copyright (c) 1996-2006 Per Bothner. All rights reserved. Your right to use such materials is set forth in the license which may be found at http:// www.gnu.org/software/ kawa/Software-License.html.
This product includes OSSP UUID software which is Copyright (c) 2002 Ralf S. Engelschall, Copyright (c) 2002 The OSSP Project Copyright (c) 2002 Cable & Wireless Deutschland. Permissions and limitations regarding this software are subject to terms available at http://www.opensource.org/licenses/mit-license.php.
This product includes software developed by Boost (http://www.boost.org/) or under the Boost software license. Permissions and limitations regarding this software are subject to terms available at http:/ /www.boost.org/LICENSE_1_0.txt.
This product includes software copyright (c) 1997-2007 University of Cambridge. Permissions and limitations regarding this software are subject to terms available at http:// www.pcre.org/license.txt.
This product includes software copyright (c) 2007 The Eclipse Foundation. All Rights Reserved. Permissions and limitations regarding this software are subject to terms available at http:// www.eclipse.org/org/documents/epl-v10.php.
This product includes software licensed under the terms at http://www.tcl.tk/software/tcltk/license.html, http://www.bosrup.com/web/overlib/?License, http://www.stlport.org/doc/ license.html, http:// asm.ow2.org/license.html, http://www.cryptix.org/LICENSE.TXT, http://hsqldb.org/web/hsqlLicense.html, http://httpunit.sourceforge.net/doc/ license.html, http://jung.sourceforge.net/license.txt , http://www.gzip.org/zlib/zlib_license.html, http://www.openldap.org/software/release/license.html, http://www.libssh2.org, http://slf4j.org/license.html, http://www.sente.ch/software/OpenSourceLicense.html, http://fusesource.com/downloads/license-agreements/fuse-message-broker-v-5-3- license-agreement; http://antlr.org/license.html; http://aopalliance.sourceforge.net/; http://www.bouncycastle.org/licence.html; http://www.jgraph.com/jgraphdownload.html; http://www.jcraft.com/jsch/LICENSE.txt; http://jotm.objectweb.org/bsd_license.html; . http://www.w3.org/Consortium/Legal/2002/copyright-software-20021231; http://www.slf4j.org/license.html; http://nanoxml.sourceforge.net/orig/copyright.html; http://www.json.org/license.html; http://forge.ow2.org/projects/javaservice/, http://www.postgresql.org/about/licence.html, http://www.sqlite.org/copyright.html, http://www.tcl.tk/software/tcltk/license.html, http://www.jaxen.org/faq.html, http://www.jdom.org/docs/faq.html, http://www.slf4j.org/license.html; http://www.iodbc.org/dataspace/iodbc/wiki/iODBC/License; http://www.keplerproject.org/md5/license.html; http://www.toedter.com/en/jcalendar/license.html; http://www.edankert.com/bounce/index.html; http://www.net-snmp.org/about/license.html; http://www.openmdx.org/#FAQ; http://www.php.net/license/3_01.txt; http://srp.stanford.edu/license.txt; http://www.schneier.com/blowfish.html; http://www.jmock.org/license.html; http://xsom.java.net; and http://benalman.com/about/license/; https://github.com/CreateJS/EaselJS/blob/master/src/easeljs/display/Bitmap.js; http://www.h2database.com/html/license.html#summary; and http://jsoncpp.sourceforge.net/LICENSE.
This product includes software licensed under the Academic Free License http://www.opensource.org/licenses/afl-3.0.php), the Common Development and Distribution License (http://www.opensource.org/licenses/cddl1.php) the Common Public License (http://www.opensource.org/licenses/cpl1.0.php), the Sun Binary Code License Agreement Supplemental License Terms, the BSD License (http:// www.opensource.org/licenses/bsd-license.php) the MIT License (http://www.opensource.org/licenses/mit-license.php) and the Artistic License (http://www.opensource.org/licenses/artistic-license-1.0).
This product includes software copyright (c) 2003-2006 Joe WaInes, 2006-2007 XStream Committers. All rights reserved. Permissions and limitations regarding this software are subject to terms available at http://xstream.codehaus.org/license.html. This product includes software developed by the Indiana University Extreme! Lab. For further information please visit http://www.extreme.indiana.edu/.
This Software is protected by U.S. Patent Numbers 5,794,246; 6,014,670; 6,016,501; 6,029,178; 6,032,158; 6,035,307; 6,044,374; 6,092,086; 6,208,990; 6,339,775; 6,640,226; 6,789,096; 6,820,077; 6,823,373; 6,850,947; 6,895,471; 7,117,215; 7,162,643; 7,243,110, 7,254,590; 7,281,001; 7,421,458; 7,496,588; 7,523,121; 7,584,422; 7676516; 7,720,842; 7,721,270; and 7,774,791, international Patents and other Patents Pending.
DISCLAIMER: Informatica Corporation provides this documentation "as is" without warranty of any kind, either express or implied, including, but not limited to, the implied warranties of noninfringement, merchantability, or use for a particular purpose. Informatica Corporation does not warrant that this software or documentation is error free. The information provided in this software or documentation may include technical inaccuracies or typographical errors. The information in this software and documentation is subject to change at any time without notice.
NOTICES
This Informatica product (the "Software") includes certain drivers (the "DataDirect Drivers") from DataDirect Technologies, an operating company of Progress Software Corporation ("DataDirect") which are subject to the following terms and conditions:
1. THE DATADIRECT DRIVERS ARE PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.
2. IN NO EVENT WILL DATADIRECT OR ITS THIRD PARTY SUPPLIERS BE LIABLE TO THE END-USER CUSTOMER FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, CONSEQUENTIAL OR OTHER DAMAGES ARISING OUT OF THE USE OF THE ODBC DRIVERS, WHETHER OR NOT INFORMED OF THE POSSIBILITIES OF DAMAGES IN ADVANCE. THESE LIMITATIONS APPLY TO ALL CAUSES OF ACTION, INCLUDING, WITHOUT LIMITATION, BREACH OF CONTRACT, BREACH OF WARRANTY, NEGLIGENCE, STRICT LIABILITY, MISREPRESENTATION AND OTHER TORTS.
- Table of Contents
- 1. Introduction
- 2. Conceptual View
- 3. Running the UM Gateway
- 4. UM Gateway Configuration
- 5. UM Gateway Examples
- 6. UM Gateway Web Monitor
1. Introduction
The Ultra Messaging® Gateway facilitates WAN routing in the absence of multicast routing capability (often due to technical obstacles or enterprise policies). The UM Gateway forwards multicast and/or unicast topic resolution advertisements and queries (TIR/TQR), which ensures that receivers in disjoint topic resolution domains from the source can receive the topic messages to which they subscribe. The UM Gateway design includes the following features.
-
Full bidirectional forwarding
-
Multi-hop forwarding
-
Support for wildcard receivers
-
Support of Request/Response messages
-
Traffic filtering on multiple criteria
-
Gateway resilience
-
UM transport monitoring statistics
-
Gateway Web Monitor
Note: The Ultra Messaging Gateway is not supported on the HP NonStop® platform.
The following features are not supported or partially supported in the 5.2 (or earlier) release of the UM Gateway.
-
Persistence
-
Mesh, loop, or alternate path gateway configurations
-
Queuing
-
Gateway Failover
-
MIM
-
JMS
-
Ultra Load Balancing (ULB)
Full Gateway support of these features is in development. If you desire any of these features or any configuration or topology not presented in this document, please contact Informatica Ultra Messaging Support for possible alternatives.
2. Conceptual View
The UM Gateway bridges disjoint topic resolution domains by effectively forwarding multicast and/or unicast topic resolution traffic, such as topic advertisements and queries (TIR/TQR), across gateways.
This section discusses the following topics.
2.1. UM Gateway Portals
A UM Gateway consists of two or more bidirectional portals that may be one of two types:
-
An endpoint portal that communicates directly to a UM topic resolution domain.
-
A peer portal that communicates only with another peer portal (of another gateway), allowing tunneling behavior between gateways or other portals.
You configure portals in the gateway's XML configuration file, specifying the portal's name, cost, UM Configuration, Access Control Lists and other attributes. See UM Gateway Configuration for more.
2.2. Topic Resolution Domains
UM contexts must satisfy the following two requirements to belong to the same topic resolution domain.
-
The contexts must use the same topic resolution UM configuration (i.e., resolver_* options are the same).
-
Contexts can communicate using the protocols required for both message transport and topic resolution traffic.
For example, two contexts on separate machines in the same LAN are not in the same topic resolution domain if they use different resolver addresses. See Multicast Resolver Network Options. A topic resolution domain can span a WAN if the UM contexts on each side of a firewall use the same UM configuration and the firewall allows UDP traffic (multicast or unicast) to pass.
Each endpoint portal must identify its associated topic resolution domain with a domain-id in the gateway's XML configuration file, as in the example below. All portals in the same topic resolution domain must have the same domain-id.
<portals>
<endpoint>
<name>LAN100</name>
<domain-id>100</domain-id>
<lbm-config>lan100.cfg</lbm-config>
</endpoint>
<endpoint>
<name>LAN200</name>
<domain-id>200</domain-id>
<lbm-config>lan200.cfg</lbm-config>
</endpoint>
</portals>
2.3. Basic Gateway Topology and Operation
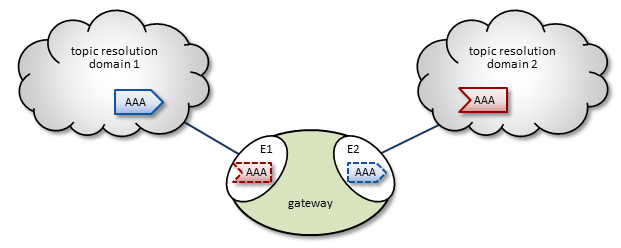
The diagram, UM Gateway, shows a UM Gateway bridging topic resolution domain 1 and topic resolution domain 2, for topic AAA. Endpoint E1 contains a proxy receiver for topic AAA and endpoint E2 has a proxy source for topic AAA.
2.3.1. Topic Resolution Across the Gateway
To establish topic resolution in an already-running UM Gateway, the following typically occurs in an example like the above figure.
-
A receiver in topic resolution domain 2 issues a TQR for topic AAA.
-
Portal E2 receives the TQR and requests that portal E1 find a TIR for AAA on topic resolution domain 1. At this point, we can say that interest for topic AAA has been discovered within the gateway.
-
E1 immediately responds with three actions: a) create a proxy receiver for topic AAA, which b) sends a TQR for AAA on domain 1, and c) issues a Topic Interest message for the benefit of any other portals that may exist in this gateway.
-
A source for topic AAA in domain 1 issues a TIR.
-
E1's AAA proxy receiver requests that E2 (and any other portals in the gateway) create a proxy source for AAA.
-
E2 creates proxy source AAA and issues a TIR to domain 2, thus completing topic resolution.
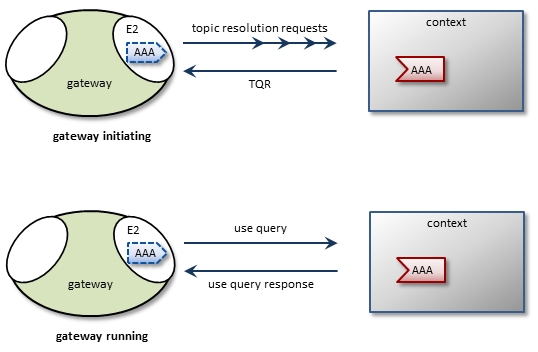
2.3.2. Interest and Use Queries
When a UM Gateway first starts, its endpoint portals issue a brief series of Topic Resolution Request messages to their respective topic resolution domains. This provokes quiescent receivers (and wildcard receivers) into sending TQRs, indicating interest in the various topics. Each portal then records this interest. The gateway uses a periodic purge cycle to detect when there is no longer any interest in the topic (i.e. all receivers for a topic have been deleted), and removes it from the portals.
After a gateway has been running, endpoint portals issue periodic Topic Use Queries and Pattern Use Queries (collectively referred to as simply Use Queries). Use Query Responses from UM contexts confirm that the receivers for these topics indeed still exist, thus maintaining these topics on the interest list. Autonomous TQRs also refresh interest and have the effect of suppressing the generation of Use Queries.
In the case of multi-hop gateway configurations, gateways cannot detect interest for remote contexts via Use Queries or TQRs. They do this instead via Interest Messages. A portal generates periodic interest messages, which are picked up by adjacent gateways (i.e., the next hop over), at which time interest is refreshed.
Intervals, limits, and durations for these topic resolution and interest mechanisms can be adjusted via gateway configuration options (see UM Gateway Configuration).
2.3.3. Gateway Keepalive
To maintain a reliable connection, gateways exchange Gateway Keepalive signals when connected via peer portals. Keepalive intervals and connection timeouts are configurable, and you can also set the gateway to send keepalives only when traffic is idle (default). See <gateway-keepalive>.
2.3.4. Proxy Sources and Receivers
The domain-id is used by Interest Messages and other internal and gateway-to-gateway traffic to ensure forwarding of all messages (payload and topic resolution) to the correct recipients. This also has the effect of not creating proxy sources/receivers where they are not needed. Thus, gateways create proxy sources and receivers based solely on receiver interest.
If more than one source sends on a given topic, the receiving portal's single proxy receiver for that topic receives all messages sent on that topic. The sending portal, however creates a proxy source for every source sending on the topic. The UM Gateway maintains a table of proxy sources, each keyed by an Originating Transport ID (OTID). This enables proxy receiver to forward each message to the correct proxy source.
Note: UM sources create a unique OTID that describes their transport sessions and include this OTID in their topic advertisements. For more on multiple sources, see Resolver Cache's Stored Cost Values Prevents Duplicates
Note: It is important to keep maximum datagram sizes exactly the same across all topic resolution domains and transports. For example, if the topic resolution domain on one side of a gateway uses LBT-RM message transport and the topic resolution domain on the other side uses LBT-RDMA, fragments from domain 1 will be too large for domain 2. See transport_*_datagram_max_size in the UM Configuration Guide.
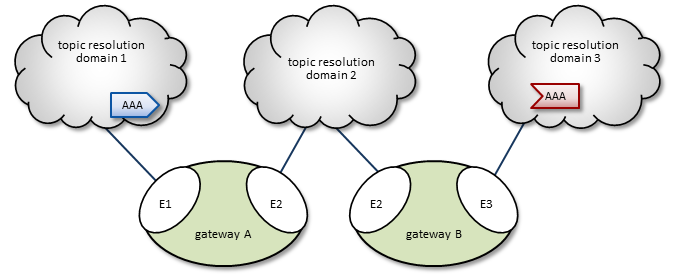
2.3.5. Multi-Hop Forwarding
Consider a simple example UM Gateway deployment, as shown in Multi-Hop Network Example.
In this diagram, gateway A has two endpoint portals, connected to topic resolution domains 1 and 2. gateway B also has two endpoint portals that bridge domains 2 and 3. (Endpoint portal names reflect the topic resolution domain to which they connect. For example, gateway A endpoint E2 interfaces topic resolution domain 2.)
Topic resolution domain 1 has a source for topic AAA, and domain 3, an AAA receiver. The following sequence of events enables the forwarding of topic messages from source AAA to receiver AAA.
-
Receiver AAA queries (issues a TQR) for a source.
-
Gateway B, endpoint E3 (B-E3) receives the TQR and requests that any other portals in the gateway forward any AAA advertisements.
-
In response, B-E2 creates a proxy receiver for AAA and sends a Topic Interest message for AAA to topic resolution domain 2. (The proxy receiver also issues a TQR.)
-
Gateway A, endpoint E2 (A-E2) receives this Topic Interest message and requests that any other portals in the gateway forward any AAA advertisements.
-
In response, A-E1 creates a proxy receiver for AAA and sends a Topic Interest message (and TQR) for AAA to domain 1.
-
Source AAA responds to the TQR by sending a TIR for topic AAA.
-
The AAA proxy receiver created by A-E1 receives this TIR and requests that all gateway A portals with an interest in topic AAA create a proxy source for AAA.
-
In response, A-E2 creates a proxy source which sends a TIR for topic AAA via domain 2.
-
The AAA proxy receiver created by B-E2 receives this TIR and requests that all gateway B portals with an interest in topic AAA create a proxy source for AAA.
-
In response, B-E3 creates a proxy source, which sends a TIR for topic AAA via domain 3.
-
Topic AAA has now been resolved across both gateways, which forward all topic messages sent by source AAA to receiver AAA.
Note: Access Control Lists can alter this sequence by, for example, accepting only certain transport types or forwarding only certain topics. For more, see Access Control Lists (ACL).
2.4. Forwarding Costs
Forwarding a message through a gateway incurs a cost in terms of latency, network bandwidth, and CPU utilization on the gateway machine, which may in turn affect the latency of other forwarded messages. Transiting multiple gateways adds even more cumulative latency to a message. Other gateway-related factors such as network bandwidth, switches, etc., can also add latency.
Factors other than latency contribute to the cost of forwarding a message. Consider a message that can be sent from one domain to its destination domain over one of two paths. A three-hop path over 1000Mbps links may be faster than a single-hop path over a 100Mbps link. Further, it may be the case that the 100Mbps link is more expensive or less reliable. These could all be reasons for favoring the longer path.
To account for these cost factors, topic advertisements (TIR) contain the following two fields.
-
hop count
-
cost
These fields appear as topic options within the TIR. When you call lbm_src_create(), UM sets both to 0 (zero) for use by the UM Gateway. You cannot set these fields; they are populated automatically by the gateway(s).
2.4.1. Hop Count
When the egress portal of a gateway creates a proxy source to forward, in effect, the original source's topic advertisement, it increments the hop count by one. In the Multi-hop example presented earlier, gateway A, endpoint E2 (A-E2) and gateway B, endpoint E3 (B-E3) would each increment the hop count, resulting in receiver AAA receiving a TIR with a hop count = 2.
2.4.2. Portal Costs
The UM Gateway lets you assign a cost to a portal. As with the hop count, when a portal creates a proxy source, it adds the portal's configured cost to the topic cost in the TIR. By default, the cost associated with a portal is 0. Using the Multi-hop example again, setting portal A-E2's cost to 3 increases the topic's cost by that much. If portal B-E3's cost is 2, the topic's cost (and TIR cost), as received by receiver AAA, is now 5. The UM Gateway uses the cost to ensure that proxy receivers connect via the most efficient path to/from their source.
Note: After paths are established, if a new lower-cost source becomes available, receivers do not switch to it.
2.4.3. Resolver Cache's Stored Cost Values Prevents Duplicates
The UM Resolver Cache stores TIRs to help receivers find sources. In addition to transport session information, the stored TIR contains the OTID, hop count and cost values. This information can be used by receivers to select the lowest cost source if a source sends over multiple network paths.
In more complex network topologies, messages from the same source may traverse multiple paths and therefore, arrive from different proxy sources and different transport sessions. If a receiver looks up a topic in the cache and finds two TIRs with the same OTID but different transport sessions, it chooses the OTID with the lowest cost and joins that transport to receive messages. This prevents receiving duplicate messages from the same source.
A UM receiver always treats advertisements for the same topic with the same OTID as equivalent transport sessions, and joins only one of them. In the event that the receiver detects an EOS on the joined transport session, one of any remaining equivalent transport sessions can be joined.
For Multicast Immediate Messages (MIM) traffic, UM receivers keep a sequence number map for every OTID they have received messages from and reject any messages that have already been received.
2.4.4. Applications Can Also Set the Topic Cost
Your application can change the cost of a topic in the receiving application's context using a callback ( source_cost_evaluation_function) that the UM Gateway uses in lbm_src_cost_function_cb(). The gateway invokes this function whenever it receives an advertisement containing cost information. With a multiple-path topology, the gateway always forwards advertisements and messages via the least costly path, using lbm_src_cost_function_cb() to determine the cost.
You can supply a callback with source_cost_evaluation_function to affect this cost determination, increasing the cost of less desirable paths or completing filtering out certain paths. The gateway passes the topic name, hop count, and cost to the configured callback, which returns an integral cost value the gateway assigns to the topic. If you do not set source_cost_evaluation_function, a default function returns the cost as passed to it.
Note: Your gateway application cannot directly configure the cost in a TIR; this is done by only the gateway itself.
2.5. Access Control Lists (ACL)
You can apply Access Control Lists (ACL) to a gateway's portals to filter or load balance traffic by certain topics, transports, topic patterns, multicast groups, etc. You configure ACLs in a gateway's XML configuration file, as children of an <endpoint> or <peer> portal. As traffic arrives at the portal, the portal either forwards it or rejects it per ACL criteria.
Inbound ACLs determine what information to forward to other portals in the gateway, while Outbound ACLs determine (by topic) what information from other portals that this portal can forward out the gateway. Each portal (endpoint or peer) can have up to one inbound ACL and one outbound ACL.
An ACL can contain one or more Access Control Entries (ACEs). ACEs let you match (and accept or reject based on), criteria elements called Access Control Conditions (ACCs). Possible ACCs are:
-
<multicast-group/> *
-
<pcre-pattern> (PCRE wildcard patterns)
-
<regex-pattern> (Regex wildcard patterns)
-
<source-ip/> *
-
<tcp-source-port/> *
-
<topic>
-
<transport/> *
-
<udp-destination-port/> *
-
<udp-source-port/> *
-
<xport-id/> * (for LBT-IPC traffic)
* These items apply to only inbound ACLs, and are ignored if used with an outbound ACL.
The above elements are all children of the <ace> element. When an ACL has multiple ACE entries, the UM Gateway goes down the list until it finds a match. It then accepts (forwards) or rejects, and is done with that ACL. An implicit "reject all" is at the end of every ACL, so the UM Gateway rejects any topic not matched. If you place multiple ACCs within an ACE, the gateway performs an "and" operation with them.
Note that the portal ignores an ACC if a) it is inbound-only and used in an outbound ACL, or b) it simply does not apply (such as a <udp-source-port/> if the transport is TCP).
Consider the following example, where we configure a portal to forward on specific topics. This example also illustrates the parent/child hierarchy for ACLs, ACEs, and ACCs.
<endpoint>
<name>LAN1</name>
<lbm-config>lan1.cfg</lbm-config>
<domain-id>1</domain-id>
<acl>
<inbound>
<ace match="accept">
<topic>ABC</topic>
</ace>
<ace match="accept">
<topic>DEF</topic>
<transport value=lbt-rm comparison=eq/>
</ace>
<ace match="accept">
<topic>GHI</topic>
</ace>
</inbound>
</acl>
</endpoint>
The above example shows each topic match in a separate ACE. When topic "GHI" arrives, the portal finds a match in the third ACE and forwards the topic. (Placing all three <topic>s in a single ACE would never match anything.) Also note that "DEF" is forwarded only if it uses an LBT-RM transport.
Since the behavior for multiple ACEs is "first match, then done", list ACEs in a specific-to-general order. For the example below, to forward topic "ABC123" but reject similar topics such as "ABCD123" or "ABCE123", list the ACE for "ABC123" first (as done below). If the ACE to reject "ABC.*123" was listed first, it would also (undesirably) match and reject "ABC123".
<endpoint>
<name>LAN1</name>
<lbm-config>lan1.cfg</lbm-config>
<domain-id>1</domain-id>
<acl>
<inbound>
<ace match="accept">
<topic>ABC123</topic>
</ace>
<ace match="reject">
<pcre-pattern>ABC.*123</pcre-pattern>
</ace>
</inbound>
</acl>
</endpoint>
You could also filter on certain transport types to accept multicast traffic but reject tcp traffic, as shown below.
<endpoint>
<name>LAN1</name>
<lbm-config>lan1.cfg</lbm-config>
<domain-id>1</domain-id>
<acl>
<inbound>
<ace match="accept">
<transport comparison="equal" value="lbtrm"/>
</ace>
<ace match="reject">
<transport comparison="equal" value="tcp"/>
</ace>
</inbound>
</acl>
</endpoint>
2.6. Response Forwarding
For request/response, the gateway appears as the responder from the perspective of the requester, and as the requester from the perspective of the responder. The UM Gateway supports request/response directly by maintaining a map between the original requester and the proxy request object it creates. The UM Gateway modifies requests and responses to appear as if they originated from the gateway.
2.7. Multicast Immediate Messaging Considerations
Multicast Immediate Messages (MIM) flood through the UM Gateway. You cannot filter MIM with Access Control Lists (ACL). Receivers on the other side of the gateway can easily receive duplicate messages. Informatica does not recommend using MIM for messaging traffic across the UM Gateway. MIM is intended for short-lived topics and applications that cannot tolerate a delay between source creation and the sending of the first message. See also Multicast Immediate Messaging.
2.8. Wildcard Receivers
The UM Gateway supports wildcard receivers, provided wildcard topic querying is not disabled. The gateway processes wildcard queries, replicating the functionality in the UM topic resolution wildcard processing. The UM Gateway creates a single proxy receiver for each topic, including topics that match one or more wildcard patterns.
2.9. TCP Connections for Tunneling
A UM Gateway peer portal communicates with exactly one peer portal on another gateway. Peer portals utilize TCP connections for all data and control traffic. (UDP is not supported for this.) Between the peer portals, you can configure either a single TCP connection, or dual TCP, with one connection serving each direction. The UM Gateway supports one tunnel per peer portal pair, and multiple peer portals.
Below is an example of a two companion peer portals (on different gateways) configured (via gateway XML configuration file) for dual TCP connections. The companion peer portal (at the other end of the tunnel) would have its sockets defined inversely.
<portals>
<peer>
<name>TUNNEL_TO_LAN2</name>
<tcp>
<interface>10.30.3.0/24</interface>
<listen-port>26123</listen-port>
<companion>
<address>10.30.3.88</address>
<port>26124</port>
</companion>
</tcp>
</peer>
</portals>
<portals>
<peer>
<name>TUNNEL_TO_LAN1</name>
<tcp>
<interface>10.30.3.0/24</interface>
<listen-port>26124</listen-port>
<companion>
<address>10.30.3.89</address>
<port>26123</port>
</companion>
</tcp>
</peer>
</portals>
For an example of a single TCP setup, see below.
<portals>
<peer>
<name>TUNNEL_TO_LAN2</name>
<single-tcp>
<interface>10.30.3.0/24</interface>
<initiator>
<address>10.30.3.88</address>
<port>26123</port>
</initiator>
</single-tcp>
</peer>
</portals>
<portals>
<peer>
<name>TUNNEL_TO_LAN1</name>
<single-tcp>
<interface>10.30.3.0/24</interface>
<acceptor>
<listen-port>26123</listen-port>
</acceptor>
</single-tcp>
</peer>
2.10. Gateway Resilience
The UM Gateway supports resilience by way of parallel paths between topic resolution domains. This technique is referred to as Replication. Each gateway forwards traffic in a normal manner, and receivers are responsible for discarding duplicate messages. A similar approach can be taken for peer portals, in which case two gateways are required for each path, for a total of four gateways.
Important: Although it is possible to configure multiple paths between topic resolution domains, configurations that result in loops or meshes are not supported. Please contact Informatica Ultra Messaging Support.
2.10.1. Resilience Considerations
You should consider the following issues when developing your approach to gateway resilience.
2.10.1.1. Traffic Volume
Any time there exists more than one path a message can take from one point to another, the possibility exists that the message will take more than one path. Due to duplicate detection, an individual receiver will only receive each message once. However, depending on the type of transport, the message may still appear on the network multiple times.
2.10.1.2. Data Session Re-establishment
When multiple paths exist from a source to a receiver, multiple proxy sources may be created adjacent to the receiver domain, appearing to the receiver as distinct but equivalent sources for the same topic. Topic resolution establishes a receiver for one such source. If one of the gateways fails, upon an EOS for the affected transport sessions, the receiver joins an equivalent transport session and continues to receive data from the remaining proxy sources, subject to EOS timeouts.
2.10.1.3. Unicast Control Session Re-establishment
While a receiver can participate in multiple channels for the same topic, this is not possible with unicast control sessions. For example, even if two adjacent gateways both proxy the same store via different paths, a receiver can only connect to one proxy at a time. This means that, regardless of whether you chose replication or redundancy, the loss of one adjacent gateway may cause a brief pause while unicast control sessions re-establish.
2.11. Gateway Monitoring
The UM Gateway provides the following monitoring facilities.
-
Gateway-specific statistics which include the number of topics and topic patterns in the topic map, along with activity statistics about all the portals configured for the gateway. See UM Gateway Web Monitor.
-
Standard UM transport statistics for the transport sessions the gateway has joined. See Spanning Two LANs for an example.
3. Running the UM Gateway
- Table of Contents
- tnwgd -- UM Gateway Daemon
tnwgd
Description
Gateway services are provided by tnwgd. A gateway configuration file is required. The contents and format of the configuration file are documented separately.
The DTD used to validate a configuration file will be dumped to standard output with
-d or --dump-dtd. After dumping
the DTD, tnwgd exits instead of providing gateway services as
usual.
The configuration file will be validated against the DTD if either the -v or --validate options are given.
After attempting validation, tnwgd exits instead of providing
gateway services as usual. The exit status will be 0 for a configuration file
successfully validated by the DTD, and non-zero otherwise.
tnwgd normally remains attached to the controlling terminal
and runs until interrupted. If the -f or --detach options are given, tnwgd instead
forks, detaches the child from the controlling terminal, and the parent exits
immediately.
Command line help is available with -h or --help.
4. UM Gateway Configuration
The UM Gateway configuration is controlled via an XML configuration file. The DTD for the UM Gateway configuration file is described in the DTD reference.
Several example UM Gateway configuration files, along with detailed explanations, can be found in UM Gateway Examples.
Note: Before designing any UM Gateway implementations based on configurations or examples other than those presented in this document, please contact your technical support representative.
4.1. Using UM XML Configuration Files with the UM Gateway
With the <lbm-config> element, you can import configurations from either a plain text or XML UMconfiguration file. However, using XML configuration files provides the following advantages over plain text UM configuration files.
-
UM attributes can be applied per topic and/or per context.
-
Attributes applied to all portals on a particular gateway can be inherited from an UM XML template, instead of being set for each individual portal.
See XML Configuration Files for more information about UM XML configuration.
Note: You should use UM XML templates to set options for individual portals because the UM Gateway processes UM XML configuration files in the <daemon> element and not within each portal's configuration as with plain text UM configuration files.
Note: Each gateway endpoint must have its request_tcp_interface option set when the gateway starts, therefore, you must set it in each <endpoint> element of the UM Gateway XML configuration file and not in an UM XML configuration file, which is implemented when the gateway creates UM objects such as proxy sources and receivers,
<endpoint> <name>Endpoint-1</name> <domain-id>1</domain-id> <lbm-attributes> <option name="request_tcp_interface" scope="context" value="10.29.3.0/24" /> </lbm-attributes> </endpoint>
4.1.1. Setting Individual Endpoint Options
When setting endpoint options, name the context of each endpoint in the gateway's XML configuration file.
<portals>
<endpoint>
<name>Endpoint_1</name>
<domain-id>1</domain-id>
<source-context-name>endpt_1</source-context-name>
<lbm-attributes>
<option name="request_tcp_interface" scope="context" value="#.#.#.0/24" />
</lbm-attributes>
</endpoint>
<endpoint>
<name>Endpoint_2</name>
<domain-id>2</domain-id>
<receiver-context-name>endpt_2</source-context-name>
<lbm-attributes>
<option name="request_tcp_interface" scope="context" value="#.#.#.0/24" />
</lbm-attributes>
</endpoint>
</portals>
Then assign configuration templates to those contexts in the UM XML configuration file.
<application name="tnwgd" template="global">
<contexts>
<context name="endpoint_1" template="endpt-1-options">
<sources />
</context>
<context name="endpoint_2" template="endpt-2-options">
<sources />
</context>
</contexts>
</application>
You specify the unique options for each of this gateway's two endpoints in the UM XML configuration <templates> section used for endpt-1-options and endpt-2-options.
4.1.2. UM Gateway and UM XML Configuration Use Cases
One advantage of using UM XML configuration files with the UM Gateway is the ability to assign unique UM attributes to the topics and contexts used for the proxy sources and proxy receivers the gateway creates. Plain text UM configuration files cannot assign UM attributes to the proxy sources and receivers based on topic. The following example shows how to assign a different LBTRM multicast address to a source based on its topic.
Create a new UM XML configuration template for the desired topic name.
<template name="custom-topic-template">
<options type="source">
<option name="transport_lbtrm_multicast_address" default-value="#.#.#.#"/>
</options>
</template>
Then include this template in the <application> element associated with the gateway.
<application name="tnwgd" template="global-options">
<contexts>
<context>
<sources template="source-options">
<topic topicname="custom_topic_name" template="custom-topic-template" />
</sources>
</context>
</contexts>
</application>
This assigns the specified UM options to sources created on a particular topic.
It is also possible to assign UM attributes directly in the <application> tag. For example, the following specifies that a particular topic should use LBTRU transport and a unicast resolver address.
<application name="tnwgd" template="tnwgd-common">
<contexts>
<context>
<sources template="source-template">
<topic topicname="LBTRU_TOPIC">
<options type="source">
<option name="transport" default-value="lbtru" />
<option name="resolver_unicast_address" default-value="#.#.#.#" />
</options>
</topic>
</sources>
</context>
</contexts>
</application>
4.1.2.1. Sample Configuration
The following sample configuration incorporates many of the examples mentioned above. The gateway applies options to all UM objects created. The UM XML configuration file overwrites these options for two specific topics. The first topic, LBTRM_TOPIC, uses a different template to change its transport from TCP to LBTRM, and to set an additional property. The second topic, LBTRU_TOPIC, also changes its transport from TCP to a new value. However, its new attributes are applied directly in its associated topic tag, instead of referencing a template. In addition, this sample configuration assigns all sources and receivers associated with the context endpt_1 the rm-source template.
UM XML Configuration File
<?xml version="1.0" encoding="UTF-8" ?>
<um-configuration version="1.0">
<templates>
<template name="tnwgd-common">
<options type="source">
<option name="transport" default-value="tcp" />
</options>
<options type="context">
<option name="request_tcp_interface" default-value="#.#.#.#/#" />
<option name="transport_tcp_port_low" default-value="#" />
<option name="transport_tcp_port_high" default-value="#" />
<option name="resolver_multicast_address" default-value="#.#.#.#"/>
</options>
</template>
<template name="rm-source">
<options type="source">
<option name="transport" default-value="lbtrm" />
<option name="transport_lbtrm_multicast_address" default-value="#.#.#.#"/>
</options>
</template>
</templates>
<applications>
<application name="tnwgd" template="tnwgd-common">
<contexts>
<context>
<sources template="rm-source">
<topic topicname="LBTRM_TOPIC" template="rm-source" />
<topic topicname="LBTRU_TOPIC">
<options type="source">
<option name="transport" default-value="lbtru" />
<option name="resolver_unicast_address" default-value="#.#.#.#" />
</options>
</topic>
</sources>
</context>
<context name="endpt_1" template="rm-source">
<sources template="rm-source"/>
</context>
</contexts>
</application>
</applications>
</um-configuration>
Gateway XML Configuration File
This gateway uses the above XML file, called sample-config.xml, to set its UM options. It has three endpoints, one of which has the context endpt_1.
<?xml version="1.0" encoding="UTF-8" ?>
<tnw-gateway version="1.0">
<daemon>
<log type="console"/>
<xml-config>sample-config.xml</xml-config>
</daemon>
<portals>
<endpoint>
<name>Endpoint_1</name>
<domain-id>1</domain-id>
<lbm-attributes>
<option name="context_name" scope="context" value="endpt_1" />
<option name="request_tcp_interface" scope="context" value="#.#.#.0/24" />
</lbm-attributes>
</endpoint>
<endpoint>
<name>Endpoint_2</name>
<domain-id>2</domain-id>
<lbm-attributes>
<option name="request_tcp_interface" scope="context" value="#.#.#.0/24" />
</lbm-attributes>
</endpoint>
<endpoint>
<name>Endpoint_3</name>
<domain-id>3</domain-id>
<lbm-attributes>
<option name="request_tcp_interface" scope="context" value="#.#.#.0/24" />
</lbm-attributes>
</endpoint>
</portals>
</tnw-gateway>
5. UM Gateway Examples
This section discusses the following topics.
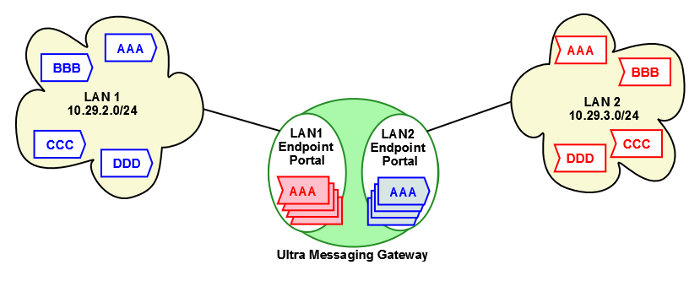
5.1. Spanning Two LANs
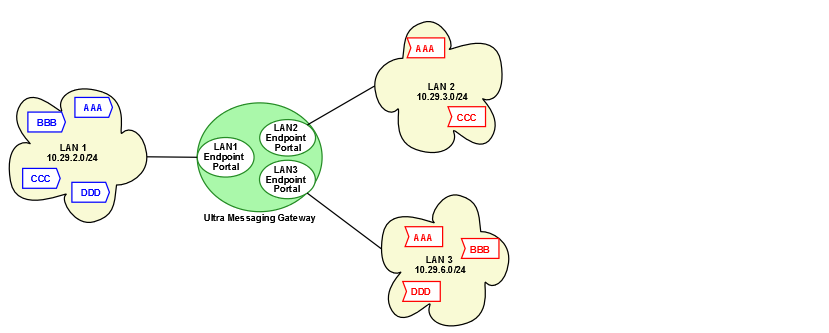
The network consists of two LANs. Within each LAN, full multicast connectivity exists. However, no multicast connectivity exists between LAN1 and LAN2. The diagram below displays proxy sources and proxy receivers in the UM Gateway.
5.1.1. UM Configuration Files
Sources in LAN1 use lan1.cfg and the receivers in LAN2 use lan2.cfg.
5.1.1.1. LAN1 Configuration
lan1.cfg
## Major Options##
source transport lbtrm
## Multicast Resolver Network Options##
context resolver_multicast_interface 10.29.2.0/24
context resolver_multicast_address 225.7.32.85
context resolver_multicast_port 13965
##Transport LBT-RM Network Options##
context transport_lbtrm_multicast_address_low 225.7.33.85
context transport_lbtrm_multicast_address_high 225.7.33.89
context transport_lbtrm_source_port_low 24000
context transport_lbtrm_source_port_high 24999
##Transport LBT-RM Operation Options##
context transport_lbtrm_data_rate_limit 100000000
context transport_lbtrm_retransmit_rate_limit 500000
receiver transport_lbtrm_activity_timeout 10000
##Transport LBT-RU Network Options##
receiver transport_lbtru_interface 10.29.2.0/24
source transport_lbtru_interface 10.29.2.0/24
##Transport LBT_RU Operation Options##
context transport_lbtru_data_rate_limit 1000000
context transport_lbtru_retransmit_rate_limit 500000
receiver transport_lbtru_activity_timeout 10000
##Multicast Immediate Messaging Network Options##
context mim_address 225.7.32.100
##Request Network Options##
context request_tcp_interface 10.29.2.0/24
##Transport TCP Network Options##
receiver transport_tcp_interface 10.29.2.0/24
source transport_tcp_interface 10.29.2.0/24
context transport_tcp_port_low 18000
context transport_tcp_port_high 18999
5.1.1.2. LAN2 Configuration
lan2.cfg
## Major Options##
source transport lbtrm
## Multicast Resolver Network Options##
context resolver_multicast_interface 10.29.3.0/24
context resolver_multicast_address 225.8.32.85
context resolver_multicast_port 13965
##Transport LBT-RM Network Options##
context transport_lbtrm_multicast_address_low 225.8.33.85
context transport_lbtrm_multicast_address_high 225.8.33.89
context transport_lbtrm_source_port_low 25000
context transport_lbtrm_source_port_high 25999
##Transport LBT-RM Operation Options##
context transport_lbtrm_data_rate_limit 100000000
context transport_lbtrm_retransmit_rate_limit 500000
receiver transport_lbtrm_activity_timeout 10000
##Transport LBT-RU Network Options##
receiver transport_lbtru_interface 10.29.3.0/24
source transport_lbtru_interface 10.29.3.0/24
##Transport LBT_RU Operation Options##
context transport_lbtru_data_rate_limit 1000000
context transport_lbtru_retransmit_rate_limit 500000
receiver transport_lbtru_activity_timeout 10000
##Multicast Immediate Messaging Network Options##
context mim_address 225.8.32.100
##Request Network Options##
context request_tcp_interface 10.29.3.0/24
##Transport TCP Network Options##
receiver transport_tcp_interface 10.29.3.0/24
source transport_tcp_interface 10.29.3.0/24
context transport_tcp_port_low 17000
context transport_tcp_port_high 17999
5.1.2. UM Gateway Configuration
This example uses the two-lans.xml configuration file, which essentially consists of two endpoint portal configurations. If you notice in the daemon section, we have turned on monitoring for the all endpoint portals in the gateway. The configuration specifies that all statistics be collected every 5 seconds and uses the lbm transport module to send statistics to your monitoring application, that runs in LAN 1. See also Monitoring LBM. The Web Monitor has also been turned on to monitor the performance of the gateway.
<?xml version="1.0" encoding="UTF-8" ?>
<!-- UM GW xml file- 2 endpoint portals -->
<tnw-gateway version="1.0">
<daemon>
<log type="console"/>
<lbm-license-file>lic0014.txt</lbm-license-file>
<monitor interval="5">
<transport-module module="lbm" options="config=lan1.cfg"/>
</monitor>
<web-monitor>*:15304</web-monitor>
</daemon>
<portals>
<endpoint>
<name>LAN1</name>
<domain-id>1</domain-id>
<lbm-config>lan1.cfg</lbm-config>
</endpoint>
<endpoint>
<name>LAN2</name>
<domain-id>2</domain-id>
<lbm-config>lan2.cfg</lbm-config>
</endpoint>
</portals>
</tnw-gateway>
5.2. Spanning Multiple LANs
The network consists of three LANs. Within each LAN, full multicast connectivity exists. However, no multicast connectivity exists between the three LANs.
5.2.1. UM Configuration Files
Sources in LAN1 use lan1.cfg and the receivers in LAN2 and LAN3 use lan2.cfg and lan3.cfg, respectively.
5.2.1.1. LAN1 Configuration
lan1.cfg
## Major Options##
source transport lbtrm
## Multicast Resolver Network Options##
context resolver_multicast_interface 10.29.2.0/24
context resolver_multicast_address 225.7.32.85
context resolver_multicast_port 13965
##Transport LBT-RM Network Options##
context transport_lbtrm_multicast_address_low 225.7.33.85
context transport_lbtrm_multicast_address_high 225.7.33.89
context transport_lbtrm_source_port_low 24000
context transport_lbtrm_source_port_high 24999
##Transport LBT-RM Operation Options##
context transport_lbtrm_data_rate_limit 100000000
context transport_lbtrm_retransmit_rate_limit 500000
receiver transport_lbtrm_activity_timeout 10000
##Transport LBT-RU Network Options##
receiver transport_lbtru_interface 10.29.2.0/24
source transport_lbtru_interface 10.29.2.0/24
##Transport LBT_RU Operation Options##
context transport_lbtru_data_rate_limit 1000000
context transport_lbtru_retransmit_rate_limit 500000
receiver transport_lbtru_activity_timeout 10000
##Multicast Immediate Messaging Network Options##
context mim_address 225.7.32.100
##Request Network Options##
context request_tcp_interface 10.29.2.0/24
##Transport TCP Network Options##
receiver transport_tcp_interface 10.29.2.0/24
source transport_tcp_interface 10.29.2.0/24
context transport_tcp_port_low 18000
context transport_tcp_port_high 18999
5.2.1.2. LAN2 Configuration
lan2.cfg
## Major Options##
source transport lbtrm
## Multicast Resolver Network Options##
context resolver_multicast_interface 10.29.3.0/24
context resolver_multicast_address 225.8.32.85
context resolver_multicast_port 13965
##Transport LBT-RM Network Options##
context transport_lbtrm_multicast_address_low 225.8.33.85
context transport_lbtrm_multicast_address_high 225.8.33.89
context transport_lbtrm_source_port_low 25000
context transport_lbtrm_source_port_high 25999
##Transport LBT-RM Operation Options##
context transport_lbtrm_data_rate_limit 100000000
context transport_lbtrm_retransmit_rate_limit 500000
receiver transport_lbtrm_activity_timeout 10000
##Transport LBT-RU Network Options##
receiver transport_lbtru_interface 10.29.3.0/24
source transport_lbtru_interface 10.29.3.0/24
##Transport LBT_RU Operation Options##
context transport_lbtru_data_rate_limit 1000000
context transport_lbtru_retransmit_rate_limit 500000
receiver transport_lbtru_activity_timeout 10000
##Multicast Immediate Messaging Network Options##
context mim_address 225.8.32.100
##Request Network Options##
context request_tcp_interface 10.29.3.0/24
##Transport TCP Network Options##
receiver transport_tcp_interface 10.29.3.0/24
source transport_tcp_interface 10.29.3.0/24
context transport_tcp_port_low 17000
context transport_tcp_port_high 17999
5.2.1.3. LAN3 Configuration
lan3.cfg
## Major Options##
source transport lbtrm
## Multicast Resolver Network Options##
context resolver_multicast_interface 10.29.3.0/24
context resolver_multicast_address 225.9.32.85
context resolver_multicast_port 13965
##Transport LBT-RM Network Options##
context transport_lbtrm_multicast_address_low 225.9.33.85
context transport_lbtrm_multicast_address_high 225.9.33.89
context transport_lbtrm_source_port_low 25000
context transport_lbtrm_source_port_high 25999
##Transport LBT-RM Operation Options##
context transport_lbtrm_data_rate_limit 100000000
context transport_lbtrm_retransmit_rate_limit 500000
receiver transport_lbtrm_activity_timeout 10000
##Transport LBT-RU Network Options##
receiver transport_lbtru_interface 10.29.6.0/24
source transport_lbtru_interface 10.29.6.0/24
##Transport LBT_RU Operation Options##
context transport_lbtru_data_rate_limit 1000000
context transport_lbtru_retransmit_rate_limit 500000
receiver transport_lbtru_activity_timeout 10000
##Multicast Immediate Messaging Network Options##
context mim_address 225.9.32.100
##Request Network Options##
context request_tcp_interface 10.29.6.0/24
##Transport TCP Network Options##
receiver transport_tcp_interface 10.29.6.0/24
source transport_tcp_interface 10.29.6.0/24
context transport_tcp_port_low 17000
context transport_tcp_port_high 17999
5.2.2. UM Gateway Configuration
The configuration for this gateway, expressed in multiple-lans.xml also has transport statistics monitoring and the WebMonitor turned on. In addition, Late Join has been activated primarily for any receivers in LAN2 or LAN 3 that start up late. The configuration specifies that all proxy sources (pSRC) always provide Late Join service even if the original source does not. It also specifies that the pSRC forward retransmissions from the original source if the pSRC cannot fill the retransmission request itself. See also Using Late Join.
<?xml version="1.0" encoding="UTF-8" ?>
<!-- UM GW xml file- 3 endpoint portals -->
<tnw-gateway version="1.0">
<daemon>
<log type="console"/>
<lbm-license-file>lic0014.txt</lbm-license-file>
<monitor interval="5">
<transport-module module="lbm" options="config=lan1.cfg"/>
</monitor>
<web-monitor>*:15304</web-monitor>
</daemon>
<portals>
<endpoint>
<name>LAN1</name>
<domain-id>1</domain-id>
<lbm-config>lan1.cfg</lbm-config>
</endpoint>
<endpoint>
<name>LAN2</name>
<domain-id>2</domain-id>
<lbm-config>lan2.cfg</lbm-config>
<late-join provide="always" forward="yes"/>
</endpoint>
<endpoint>
<name>LAN3</name>
<domain-id>3</domain-id>
<lbm-config>lan3.cfg</lbm-config>
<late-join provide="always" forward="yes"/>
</endpoint>
</portals>
</tnw-gateway>
6. UM Gateway Web Monitor
The built-in web monitor (configured in the tnwgd XML configuration file) provides valuable statistics about the gateway and its portals, for which, the Web Monitor separates into receive statistics and send statistics. This section discusses the following topics.
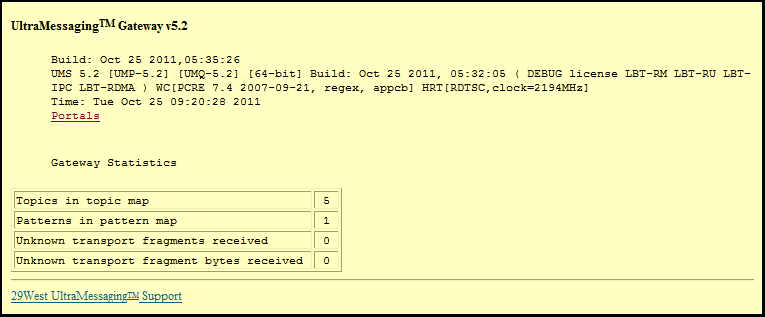
6.1. UM Gateway Web Monitor Main Page
-
This page provides statistics on the topics and wildcard patterns configured for the gateway, along with the number of unknown fragments and fragment bytes received.
-
To go to the Portals page, click on Portals.
Note: On some platforms, this page may include a link to a memory allocation display page.
6.2. UM Gateway Web Monitor Portals Page
This page allows you to link to any of the Peer or Endpoint portals configured for the gateway.
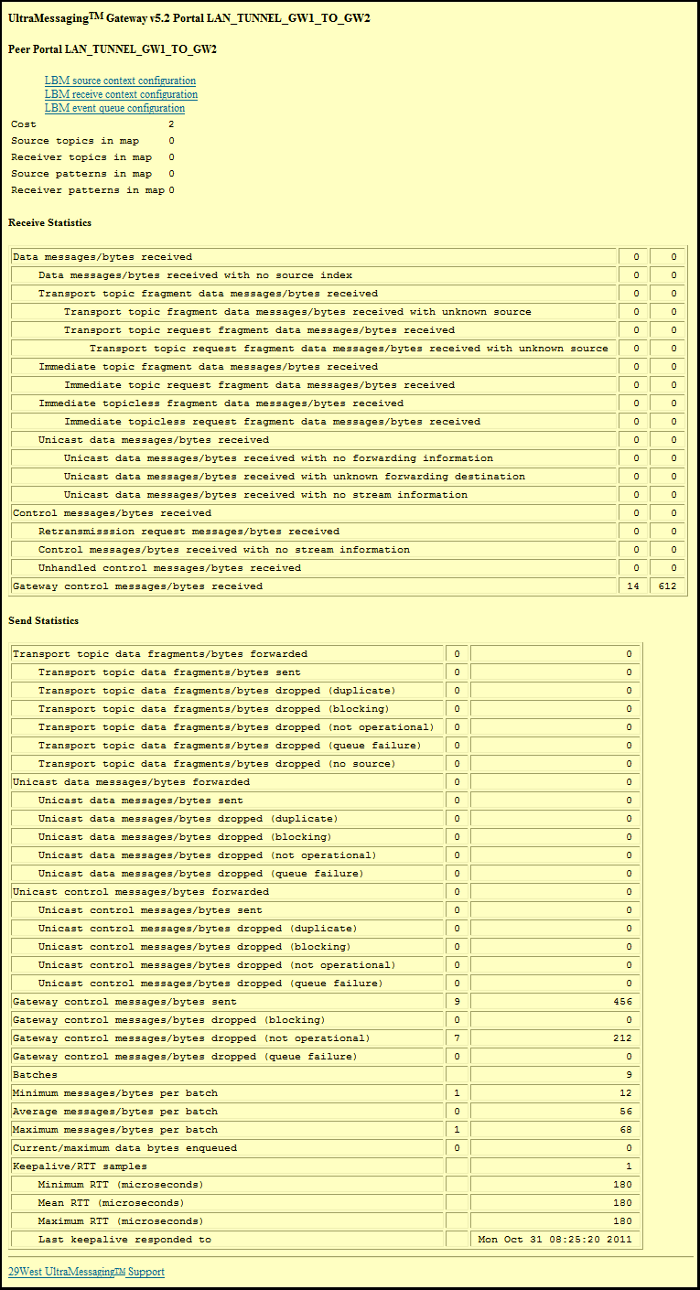
6.3. UM Gateway Web Monitor Peer Portal Page
This page allows you to see Receive and Send statistics for the selected peer portal. Click on any of the links at the top of the page to review configuration option values for the portal's UM topic resolution domain.
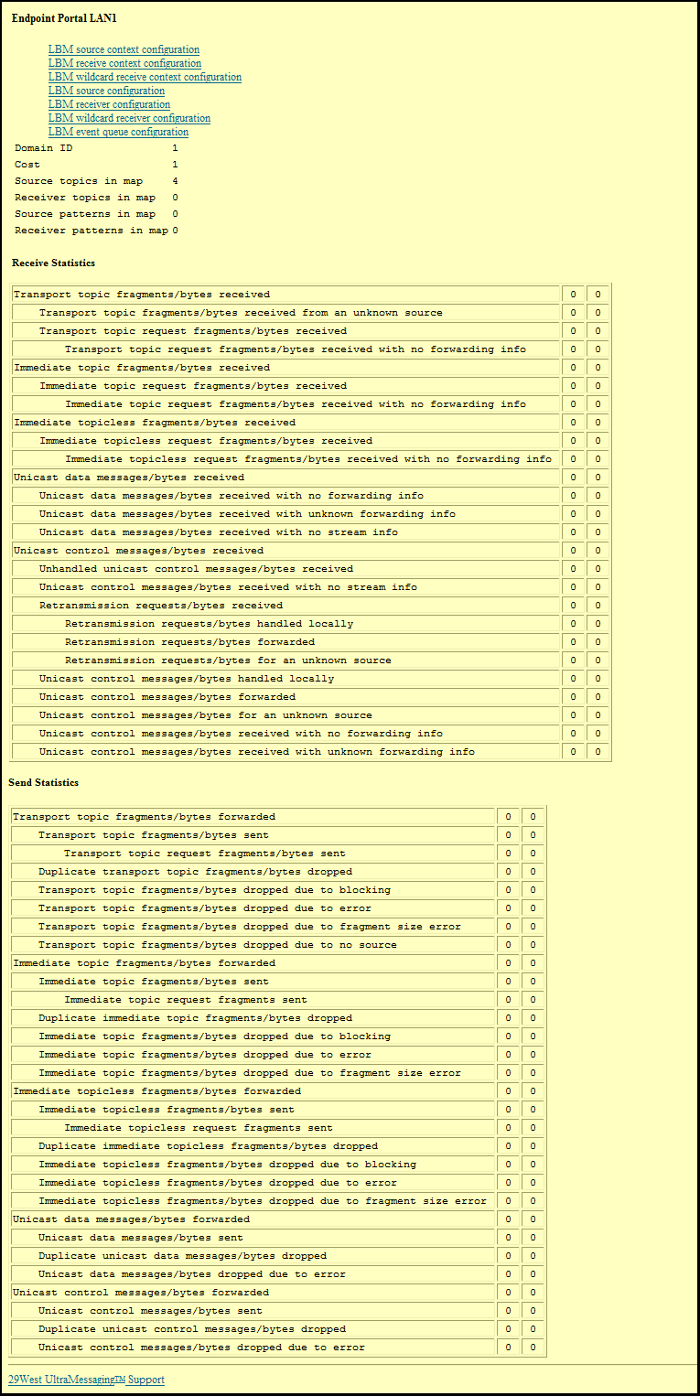
6.4. UM Gateway Web Monitor Endpoint Portal Page
This page allows you to see Receive and Send statistics for the selected endpoint portal. Click on any of the links at the top of the page to review configuration option values for the portal's UM topic resolution domain.